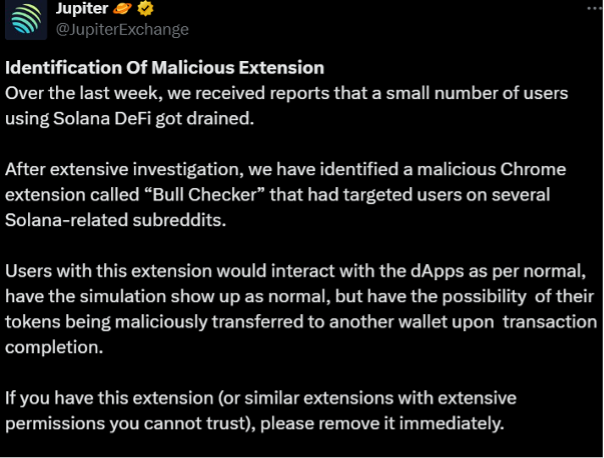
DeFi users on Solana reported having their funds drained mysteriously. A Chrome extension promoted on Reddit was a disguised crypto drainer, stealing funds by manipulating transactions. Jupiter, a DEX (decentralized exchange) aggregator, warned users of a new malware packaged as a Chrome-based extension called Bull Checker. It was advertised to serve the purpose of showing all the holders of any memecoin. Solana-based DeFi users who installed the extension reported having their assets stolen. As Jupiter’s user base interacting with the Solana DeFi ecosystem voiced similar incidents, it dug deep to find the source of the hacks. In an X post, it revealed the findings. “After extensive investigation, we have identified a malicious Chrome extension called “Bull Checker” that had targeted
Topics:
Suraj Manohar considers the following as important: Crime, crypto wallets, News, solana
This could be interesting, too:
Christian Mäder writes Bitpanda startet DeFi Wallet und öffnet die Tür zu Web3
Bitcoin Schweiz News writes OpenSea: Der Marktplatz für NFTs und digitale Sammlerstücke
Bitcoin Schweiz News writes BlackRock bringt Bitcoin-ETP nach Europa – Was bedeutet das für den Kryptomarkt?
Chayanika Deka writes XRP, SOL, and ADA Inclusion in US Crypto Reserve Pushes Traders on Edge
- DeFi users on Solana reported having their funds drained mysteriously.
- A Chrome extension promoted on Reddit was a disguised crypto drainer, stealing funds by manipulating transactions.
Jupiter, a DEX (decentralized exchange) aggregator, warned users of a new malware packaged as a Chrome-based extension called Bull Checker. It was advertised to serve the purpose of showing all the holders of any memecoin. Solana-based DeFi users who installed the extension reported having their assets stolen.
As Jupiter’s user base interacting with the Solana DeFi ecosystem voiced similar incidents, it dug deep to find the source of the hacks. In an X post, it revealed the findings. “After extensive investigation, we have identified a malicious Chrome extension called “Bull Checker” that had targeted users on several Solana-related subreddits.” Those behind the extension advertised the malicious product on Reddit, luring users in by claiming to make thousands of dollars with it.
Source: Jupiter
The post continued, “Users with this extension would interact with the dApps as per normal, have the simulation show up as normal, but have the possibility of their tokens being maliciously transferred to another wallet upon transaction completion.” It added, “If you have this extension (or similar extensions with extensive permissions you cannot trust), please remove it immediately.”
Bull Checker Asked for Permission to Change Data, Manipulated Transactions and Routed Funds to Exploiter’s Wallet
Bull Checker, upon installation, asked users for permission to read and change data, which should have tipped users off. However, many did not notice. Extensions safe for use ask to read data and nothing more. By allowing Bull Checker to alter data, it manipulates recipient addresses on transactions, sending funds from crypto transfers to a bad actor’s wallet. The concerning part is that the crypto drainer passed all simulation checks and could not be identified as a tool developed and used by nefarious entities.
In a detailed report published by Jupiter’s pseudonymous founder, who goes by Meow, wrote, “Bull Checker is supposed to be a read-only extension that allows you to view the holders of memecoins. There should be no need for an extension like this to read or write data on all websites.” They also offered words of advice to those interacting with offerings promoted in online communities, “Do not trust something just because someone mentioned it on Reddit or other media and it has many upvotes. Astroturfing and social engineering are very real.”
