A user discovered an anomaly Monday in command line interface binaries downloaded from Monero’s website.The Monero community quickly discovered malicious code. One user reported ,000 missing from their wallet.Users can take steps to verify code before running it, and additional security measures to secure their crypto.GetMonero.org, the official website of the privacy-focused Monero cryptocurrency, is down Wednesday morning, two days after a user on Github reported a miss-matched hash in command line interface binaries available for download from Monero’s website.Monero’s official website is down Wednesday morning following news of a malicious, crypto stealing hack.,000 of Monero Reported StolenA few hours later, users had determined that the anomaly was no error, but malicious code
Topics:
Wes Messamore considers the following as important: Cryptocurrency News, Github
This could be interesting, too:
Bitcoin Schweiz News writes Bitcoin & Politik: Welche US-Abgeordneten in Bitcoin investiert sind
Christian Mäder writes BitcoinRain.io: Eine Live-Visualisierung des Bitcoin-Netzwerks
Temitope Olatunji writes X Empire Unveils ‘Chill Phase’ Update: Community to Benefit from Expanded Tokenomics
Bhushan Akolkar writes Cardano Investors Continue to Be Hopeful despite 11% ADA Price Drop
- A user discovered an anomaly Monday in command line interface binaries downloaded from Monero’s website.
- The Monero community quickly discovered malicious code. One user reported $7,000 missing from their wallet.
- Users can take steps to verify code before running it, and additional security measures to secure their crypto.
GetMonero.org, the official website of the privacy-focused Monero cryptocurrency, is down Wednesday morning, two days after a user on Github reported a miss-matched hash in command line interface binaries available for download from Monero’s website.
$7,000 of Monero Reported Stolen
A few hours later, users had determined that the anomaly was no error, but malicious code planted to steal cryptocurrency. By Tuesday, Reddit user /u/moneromanz reported $7,000 worth of XMR missing from their wallet after downloading the malicious code:
I can confirm that the malicious binary is stealing coins. Roughly 9 hours after I ran the binary a single transaction drained my wallet of all $7000. I downloaded the build yesterday around 6pm Pacific time.
MoneroManz warned of the possibility that the infected code could carry out other malicious actions affecting other files on a user’s machine. They also published a copy of the malware for anyone to download and study. Cyber sleuths should be advised not to run these infected binaries on anything but a secure test computer without access to cryptocurrency wallets.
How To Keep Your Crypto Secure
This will not be the first, nor last crypto security breach, but there are measures you can take to keep your cryptocurrency secure. As it says on Blaze’s Security Blog:
Monero is not the first, nor will it likely be the last cryptocurrency (in this case, its website and binaries) that gets compromised.
Follow the steps in this blog post to protect yourself and always watch your online accounts closely…
If you hold Monero, Blaze’s blog post contains a detailed, step-by-step guide to retrace your steps and verify you’re running clean binaries on your machine.
A moderator on /r/Monero also advises Monero users to take responsibility for securing their crypto by verifying the integrity of downloaded binaries themselves before executing them:
We encourage users to check the integrity of the binaries and verify that they were signed by Fluffypony’s GPG key. A guide that walks you through this process can be found here for Windows and here for Linux and Mac OS X.
_MrBit pointed out on the subreddit Wednesday morning that using hardware wallets is more secure and offers crypto users an additional layer of protection against hacks:
And thats why you check the hash of downloads.
By the way, hardware wallets are not affected by this since you have to manually accept the outgoing transaction physically.
Monero Accused of Failing to Warn Users
An author at “Reclaim The Net” reported Tuesday that the Monero core team has been accused of failing to warn users about the malicious code available for download on its website. Noting that users on Reddit, Github and Twitter had issued warnings over the previous 24 hours, Tom Parker wrote:
While users on Reddit, Twitter, and GitHub may have seen these warnings, there are no similar warnings on GetMonero.org – the website which served this compromised code.
But officials did post a warning on GetMonero.org sometime that day. Although the website is currently down and a timestamp is not readily available to determine exactly when, a quote from the official warning with a link to the page on GetMonero was published on ArsTechnica Tuesday evening:
It’s strongly recommended to anyone who downloaded the CLI wallet from this website between Monday 18th 2:30 AM UTC and 4:30 PM UTC, to check the hashes of their binaries. If they don’t match the official ones, delete the files and download them again. Do not run the compromised binaries for any reason.
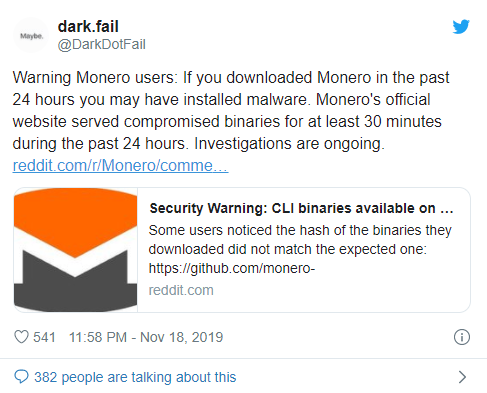
“dark.fail” admonished Monero on Twitter for taking more than 10 hours to issue a warning on its website. On /r/Monero, one user said Tuesday that they were very happy with “how fast this attack got revealed. Thumbs up for the community.”
