The AMOS stealer targets wallets on MacOS devices to drain the funds they hold. Its developers advertise it as popular applications used in the MacOS ecosystem, only to have users download the malware from spoofed sites that look like the real deal. The AMOS—short for Atomic MacOS—malware has received an upgrade that allows it to clone wallet applications on devices operating with MacOS. The group behind its development, ‘Crazy Evil,’ is advertising it via Google AdSense, masking it as popularly used apps like Loom, Callzy, and Figma. An investigation by the cybersecurity firm Moonlock showed how Crazy Evil is getting users to download the AMOS stealer. Advertisements for applications like Loom are placed on banners served by Google. Users clicking on them to download Loom or other
Topics:
Suraj Manohar considers the following as important: Hacked, News
This could be interesting, too:
Bilal Hassan writes Morocco Cracks Down on Crypto Property Deals
Bilal Hassan writes Crypto Becomes a U.S. ‘Weapon,’ Says CryptoQuant CEO
Bilal Hassan writes White House Crypto Czar Sold Holdings After Trump Took Office
Bilal Hassan writes CZ Suggests Safe Token Release Based on Price Growth
- The AMOS stealer targets wallets on MacOS devices to drain the funds they hold.
- Its developers advertise it as popular applications used in the MacOS ecosystem, only to have users download the malware from spoofed sites that look like the real deal.
The AMOS—short for Atomic MacOS—malware has received an upgrade that allows it to clone wallet applications on devices operating with MacOS. The group behind its development, ‘Crazy Evil,’ is advertising it via Google AdSense, masking it as popularly used apps like Loom, Callzy, and Figma.
An investigation by the cybersecurity firm Moonlock showed how Crazy Evil is getting users to download the AMOS stealer. Advertisements for applications like Loom are placed on banners served by Google. Users clicking on them to download Loom or other popular apps get diverted to websites that look just like the ones of the companies offering legitimate apps. However, clicking the download button brings the AMOS stealer to users’ devices, which can wreak havoc if they have wallet applications on them.
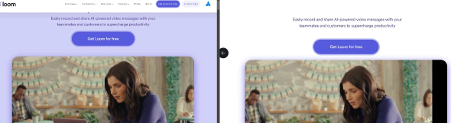
“The real Loom site can be seen to the left. The malicious, fake Loom site can be seen on the right.” Source: Moonlock’s report on the AMOS stealer.
AMOS Can Manipulate Ledger Live Successfully, Could Also Do the Same to Other Wallet Apps
The cybersecurity firm’s look at the malware suggests it can replicate Ledger Live—the software app that helps initiate transactions from hardware ledger wallets. While users’ private keys are not stored on Ledger Live, making it impossible for AMOS to steal wallet credentials, Moonlock believes AMOS can change transaction recipient addresses. It can do so while everything the wallet app displays seems highly legitimate. Users will only know that their funds were drained to addresses they did not mean to transact with after the transactions are conducted. While Moonlock has identified AMOS to target Ledger Live, it may also hold the capabilities to do the same with other popular wallets like MetaMask.
“Moonlock Lab found that this new version of AMOS has a novel capability. The malware can replace a specific crypto wallet app with a clone and easily wipe out victims’ e-wallets. This ability has never been reported in a version of AMOS before and represents a significant leap forward,” the report read.
This malware’s previous version was identified in April 2023 and reported to steal encrypted keyvault files from users’ wallets. Cybercriminals could use these files to drain user funds from their wallets. About 50 crypto wallet applications were vulnerable to the threat. Crazy Evil sold it to bad actors for $1,000 a pop. Moonlock claimed the new version is being sold at around $3,000 to cybercriminals.
