Cthulhu Stealer attacks Mac devices and steals credentials from a long list of crypto wallets. Malware aimed at draining funds from crypto wallets installed on Macs is rising. A new malware called Cthulhu Stealer targets devices with MacOS to steal crypto wallet information, marking yet another malware affecting users of Mac devices. Cado Security identified the new malware and published a report detailing how it grabs wallet data. This has come to light days after reports of another malicious program, AMOS, manipulating the Ledger Live software application for Mac emerged. “For years there has been a general belief in the Zeitgeist that macOS systems are immune to malware,” the report read. “While MacOS has a reputation for being secure, macOS malware has been trending up in recent
Topics:
Suraj Manohar considers the following as important: Crime, crypto scams, Hacked, News
This could be interesting, too:
Bilal Hassan writes Morocco Cracks Down on Crypto Property Deals
Bilal Hassan writes Crypto Becomes a U.S. ‘Weapon,’ Says CryptoQuant CEO
Dimitar Dzhondzhorov writes Watch Out: Shiba Inu (SHIB) Team Issues a Major Warning to the Community
Bilal Hassan writes White House Crypto Czar Sold Holdings After Trump Took Office
- Cthulhu Stealer attacks Mac devices and steals credentials from a long list of crypto wallets.
- Malware aimed at draining funds from crypto wallets installed on Macs is rising.
A new malware called Cthulhu Stealer targets devices with MacOS to steal crypto wallet information, marking yet another malware affecting users of Mac devices. Cado Security identified the new malware and published a report detailing how it grabs wallet data. This has come to light days after reports of another malicious program, AMOS, manipulating the Ledger Live software application for Mac emerged.
“For years there has been a general belief in the Zeitgeist that macOS systems are immune to malware,” the report read. “While MacOS has a reputation for being secure, macOS malware has been trending up in recent years,” it added.
Cthulhu Stealer disguises itself as legitimate software for MacOS, operating as an Apple Disk Image (DMG). When users open the malware application, it prompts them for their password. When they follow through, it prompts them for their MetaMask password. It then stores the sensitive wallet details in text files on their devices. The malware can also do the same for other wallets, including Atomic, Trust, Binance, Coinbase, and numerous others. It gathers other information, too, like users’ IP addresses, OS versions, hardware and software details, and more.
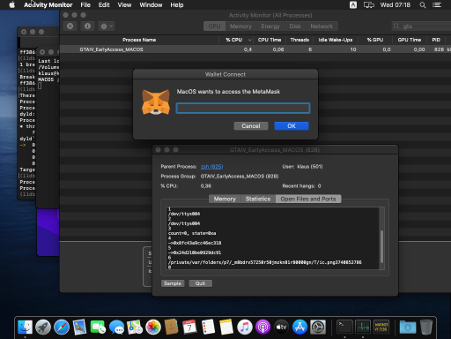
Cthulhu Stealer prompting MetaMask password. Source: Cado Security
“The main functionality of Cthulhu Stealer is to steal credentials and cryptocurrency wallets from various stores, including game accounts,” Cado mentioned. Its report elaborated on how Cthulhu Stealer is similar to another MacOS-targeting malware called the Atomic Stealer. The cybersecurity firm believes that Cthulhu is a modified version of Atomic.
The Rise of Malware-as-a-Service Offerings
Cthulhu is being sold as a Malware-as-a-Service (MaaS) product for a subscription fee of $500 every month, with subscription-based malware services growing in demand. The main developer also takes a significant portion of every exploit, paying those deploying the malware a percentage of their earnings. Cado’s investigation found that “Cthulhu stealer sold on two well-known malware marketplaces which are used for communication, arbitration and advertising of the stealer, along with Telegram.”
However, there may be trouble in paradise for those deploying the malware on victims’ devices. Many have complained about the developer pulling an exit scam and not paying them their share of the ill-gotten proceeds.
