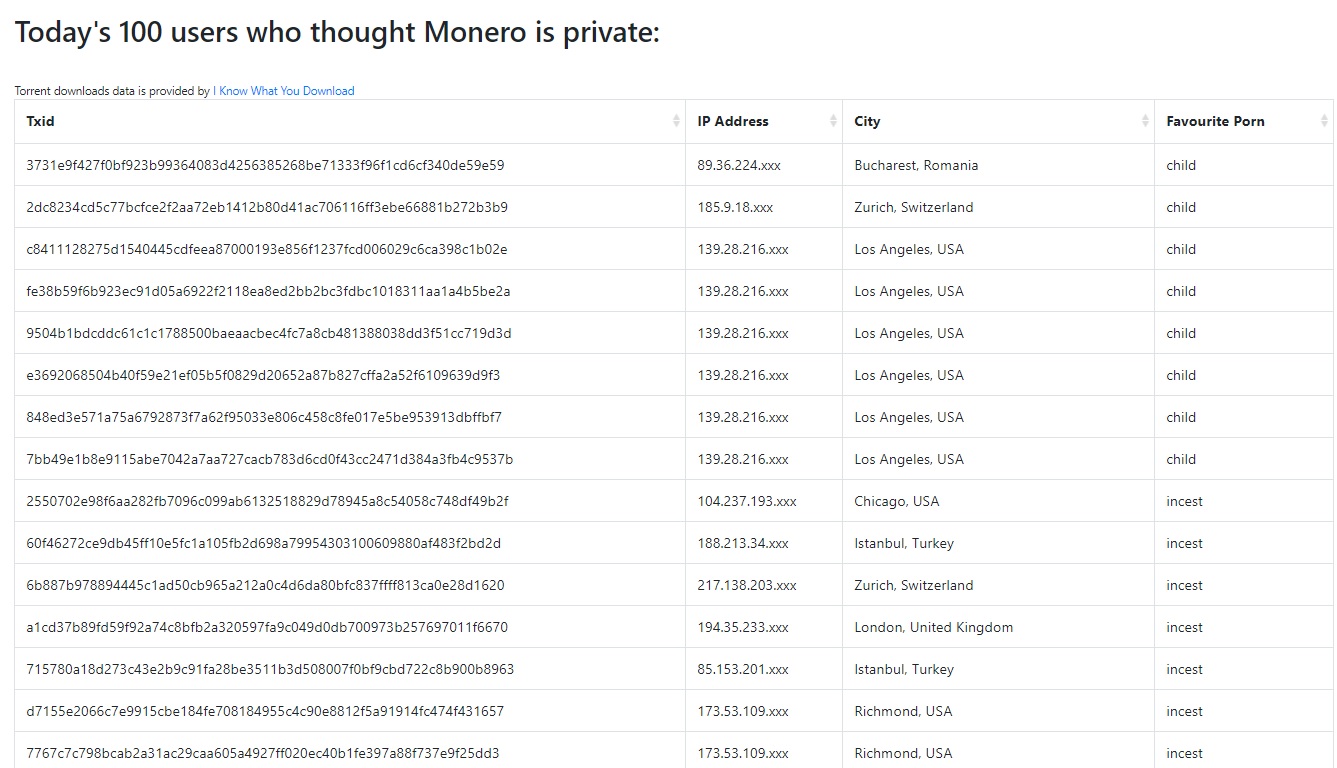
A few days ago, a mysterious Twitter user claimed to have found the magic formula to crack Monero. Fireice_UK shared a web address that “revealed” personal information of several Monero users, even including their sexual preferences. “Anonymous” cryptocurrency #Monero broken. https://t.co/M2tDXFzpLb You can now check how many paedophiles thought it is private today. 100 new IP addresses, transaction details and user’s porn preferences published every day.#SaveTheChildren $xmr — Fireice UK (@fireice_uk) November 5, 2020 The website in question, Monero BADCACA, features a table with the TxID of a Monero transaction, its city of origin, the node’s IP —perhaps not the sender’s, more on this later— and the person’s favorite porn based on the torrents they downloaded. The Dark
Topics:
Felix Mollen considers the following as important: AA News, Hacking, security, XMRBTC, XMRUSD
This could be interesting, too:
Chayanika Deka writes Yuga Labs Secures Major Win as SEC Closes Investigation Without Charges
Andrew Throuvalas writes Bitcoin Soars Back To ,000 After BlackRock CEO Says “Buy The Dip”
Chayanika Deka writes XRP, SOL, and ADA Inclusion in US Crypto Reserve Pushes Traders on Edge
Chayanika Deka writes Why Arthur Hayes Is Bullish on Bitcoin Under Trump’s Economic Strategy
A few days ago, a mysterious Twitter user claimed to have found the magic formula to crack Monero.
Fireice_UK shared a web address that “revealed” personal information of several Monero users, even including their sexual preferences.
“Anonymous” cryptocurrency #Monero broken. https://t.co/M2tDXFzpLb
You can now check how many paedophiles thought it is private today. 100 new IP addresses, transaction details and user’s porn preferences published every day.#SaveTheChildren $xmr
— Fireice UK (@fireice_uk) November 5, 2020
The website in question, Monero BADCACA, features a table with the TxID of a Monero transaction, its city of origin, the node’s IP —perhaps not the sender’s, more on this later— and the person’s favorite porn based on the torrents they downloaded.
The Dark Side of Monero?
The site also has a FAQ. Fireice_UK claims to have been tracking the blockchain for some time and that the Monero development team knew about the project’s shortcomings, basically turning a blind eye to it and caring mostly about the money:
I have been logging Monero transactions for over a year now. Main reason why I decided to go public are blatant lies that there is nothing to worry about Ciphertrace and that Monero is private.
All things considered, how did the hacker get access to this information? Another tweet could be the key to the answer: Unlike Ciphertrace, they got it from the nodes; basically intercepting the data before it spread through the network.
If your #monero transaction was stuck in the mempool for a few minutes. I have some bad news – that means it was intercepted by BADCACAhttps://t.co/zMmx9BntaN
— Fireice UK (@fireice_uk) November 5, 2020
What Actually Happened
Riccardo “fluffypony” Spagni, who served for a long time as Monero’s lead developer, explained what happened in an extensive thread. TL;DR: It’s nothing alarming, and in fact, Monero’s very design makes it virtually impossible to identify the user with certainty.
Recently, a largely incompetent attacker bumbled their way through a Sybil attack against Monero, trying to correlate transactions to the IP address of the node that broadcast it. Whilst novel in that it is the 1st Sybil attack of this sort, it was also quite ineffective. 1/n
— Riccardo Spagni (@fluffypony) November 10, 2020
A Sybil attack occurs when a malicious actor tries to obtain information from a user through various practices such as creating multiple accounts or nodes to intercept and block transactions. This can happen on many public blockchains, not just Monero.
Monero uses a transaction broadcast system called Dandelion++. Unlike Bitcoin —where a person usually broadcasts a transaction as quickly as possible to as many nodes as they can— in Monero, the transaction bounces off several individual nodes before one of them spreads it across the network.
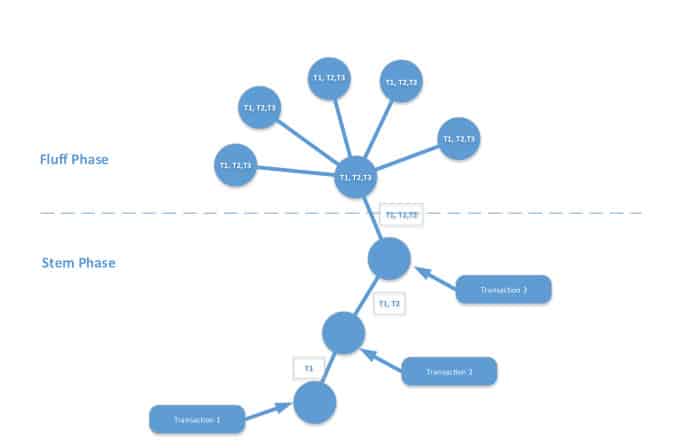
In short, the nodes can know the IP that spread the information, but are not sure if it’s the IP of who sent the transaction. In fact, intermediate nodes also don’t know if they are communicating with the sender or they’re just bouncing the information.
Therefore, the intercepted IP does not necessarily belong to the people involved in a transaction. Nor is it 100% real that fireice_UK has “broken” Monero. The amounts, addresses, and sensitive data associated with those transactions remained unknown. Equally important, what about the porn? Well: obfuscation methods like VPNs, Tor or i2p make it almost impossible to link a user to one of the IP addresses shared by BADCACA —but there’s always a chance.
Still Nervous?
Spagni explains that the hacker tried really hard in order to achieve such a difficult attack, but even after all the effort, the reliable information they were able to obtain was very little:
This attack, whilst novel in that it is a live Sybil attack against a network, was simply not large enough to be broadly effective against Dandelion++ – the attacker would have had to launch many thousands more nodes. 9/n
— Riccardo Spagni (@fluffypony) November 10, 2020
Even if they did do this, they would still not have been able to demonstrably prove a link between a node and a transaction, and it would be a “best guess” heuristic. Naturally this attack was entirely useless against anyone using a light node (eg. MyMonero), 10/n
— Riccardo Spagni (@fluffypony) November 10, 2020
against anyone using Tor / i2p for their node, against anyone who runs their node behind a VPN, or against anyone using pushtx on a Monero block explorer to broadcast their transactions. It was also largely useless for anyone using a node remotely (eg. Monerujo or the GUI). 11/n
— Riccardo Spagni (@fluffypony) November 10, 2020
In other words, it seems like there is nothing to fear, but if the possibility of a Sybil attack worries you, just follow some essential tips:
- Run your own node
- Broadcast your transactions on a block explorer’s pushtx functionality
- Use Tor or i2p
- Get a girlfriend and stop downloading porn